Our philosophy
Our goal: utilizing experiences while honestly acting in accordance with one’s own strengths and weaknesses. External support works best when deep expert knowledge, consulting methods and good timing come together.
We want to follow this path of professional craft enriched by concise and detailed knowledge.
Experts
- are acknowledged experts
- understand operational needs and restrictions
- command a wealth of experience-based solutions
- think in technical answers, rarely monetary one.
Consultants
- are experienced in structuring and supporting teams
- are masters in abstracting and putting in a nutshell
- have seen a great deal of companies and their ways of doing things
- help implementing painful change.

Our Services
Functions
Regions
Industries/chemicals
Pharmaceuticals
Infrastructure and Site Services
Competencies (industry knowledge & digitalization impact)
Governance and process optimization

Our NIS2 Compliance Service Offering:
Achieve NIS2 Readiness: From Compliance Risk to Cyber Resilience
The EU’s NIS2 Directive is mandatory for thousands of medium and large enterprises, elevating cybersecurity to a C-suite concern with the threat of severe penalties (up to 2% of global turnover) and personal liability for management . Given the lack of transition periods in the upcoming national law (NIS2UmsuCG), immediate action is critical.
Our 3-Phase NIS2 Implementation Roadmap
We provide comprehensive expertise to ensure your security program is robust, verifiable, and aligned with all mandatory requirements.
Phase 1: Strategic Assessment & Planning (This phase establishes the foundation for your compliance project):
- Applicability & Gap Analysis:
We confirm your status (Essential or Important Entity) and conduct a systematic assessment (Gap Analysis) against the NIS2 requirements. - Risk Prioritization:
We perform a comprehensive risk assessment to identify and prioritize critical vulnerabilities, delivering a detailed, resource-optimized remediation plan.
Phase 2: Implementation & Execution (We implement the mandatory technical and organizational measures):
- Technical Controls: Deployment of core security measures, including Multi-Factor Authentication (MFA), encryption, and network segmentation.
- Supply Chain Security: Assessment of your third-party providers and integration of mandatory security standards into supplier contracts.
- Governance & Training: Formal establishment of an ISMS foundation, creation of robust Incident Response (IR) and Business Continuity Plans (BCM), and mandatory, role-based training for employees and management.
Phase 3: Validation & Audit-Readiness (This phase ensures sustained compliance and readiness for regulatory scrutiny):
- Testing & Audit: We perform internal audits and penetration tests to verify the effectiveness of all implemented controls.
- Documentation & Reporting: Creation and maintenance of comprehensive compliance documentation and establishing processes for the timely, multi-stage notification of significant incidents (24h/72h/1 month) to national authorities.
Our Strategic Differentiation
Expacon GmbH offers deep specialization in the most complex NIS2 areas, including securing Operational Technology (OT) environments (e.g., manufacturing and energy) and advanced Cyber Supply Chain Risk Management (C-SCRM).
Partner with Expacon GmbH today to secure your digital future and protect your leadership from liability.
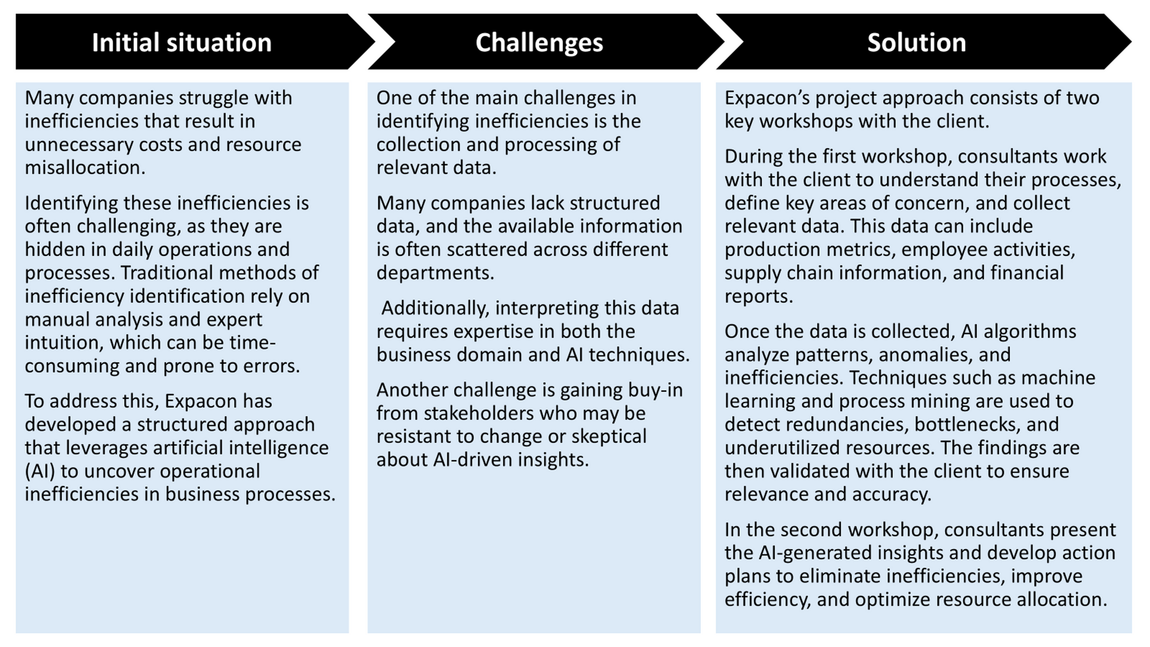
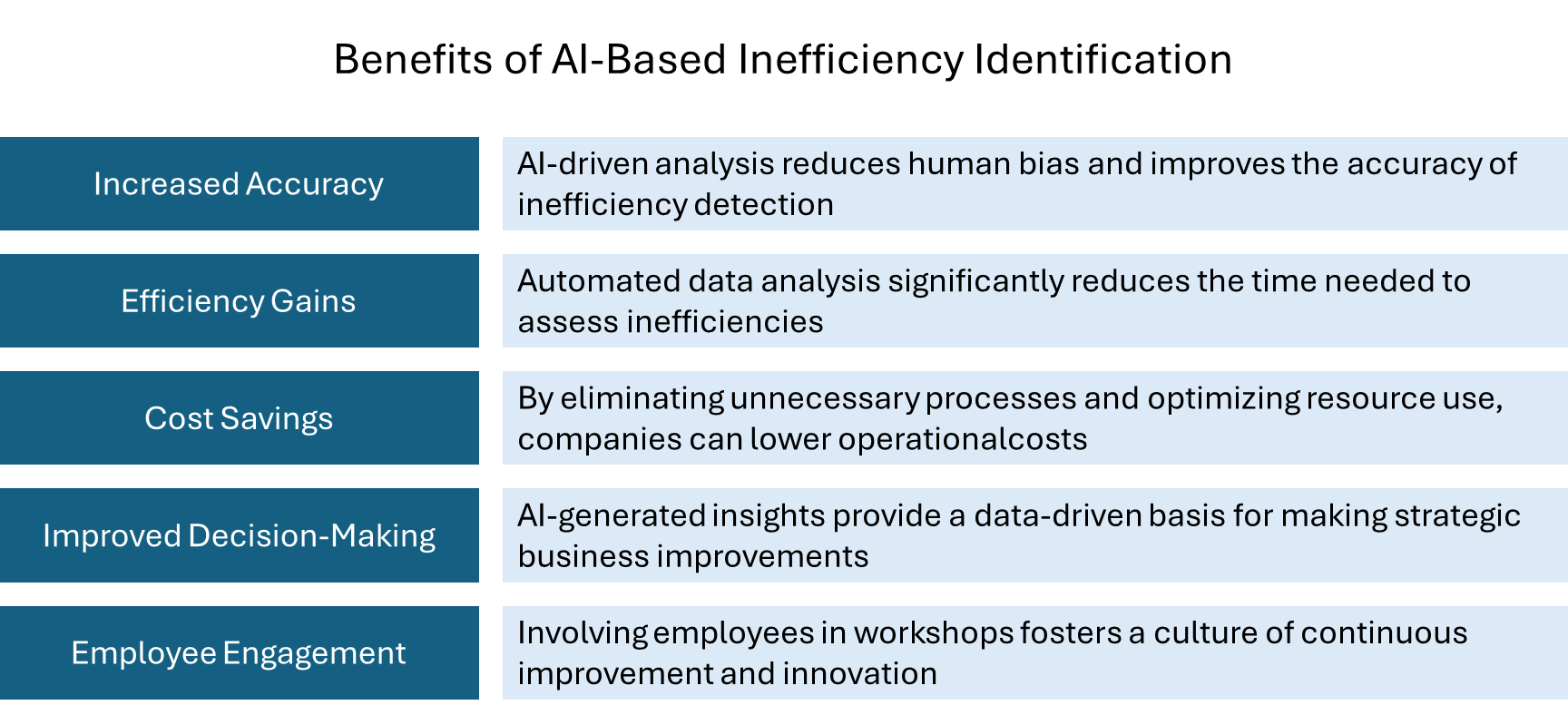
Using AI to Identify Inefficiencies
(Small-Scale Pilot Projects)
Do you have questions regarding the
German Supply Chain Act (Lieferkettensorgfaltspflichtgesetz)?
__________________________________________________________________________________________________________________________
Five elements have to be prepared to fulfill the German Supply Chain Act:

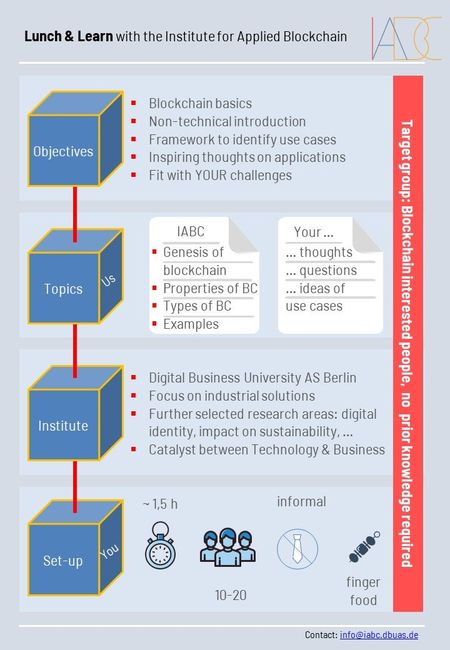
Lunch & Learn about Blockchain
S4HANA - your chance to cut off old pigtails


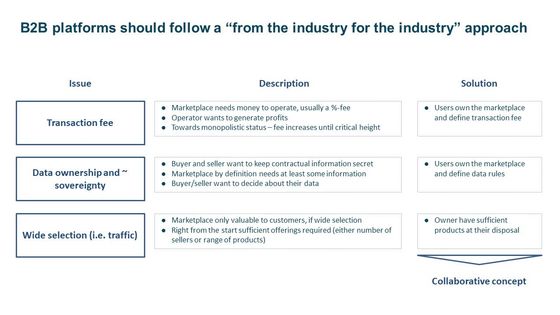
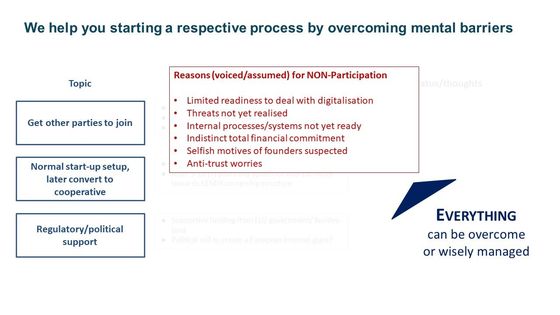
Introductory discussion on marketplaces